
Why should you care about 2FA?
When you think of how much you do online or on your phone, there is always a real threat that there is someone out there trying to find ways to take your hard-earned dollar or steal valuable information. The facts are simple; if you use the internet, there is a good chance your data is at risk. The next logical step is to take precautions to secure your information. Many organisations have already addressed this threat by implementing 2FA. Organisations you may recognise include Xero, MYOB, various banks, Google and social media sites.
So what is 2FA?
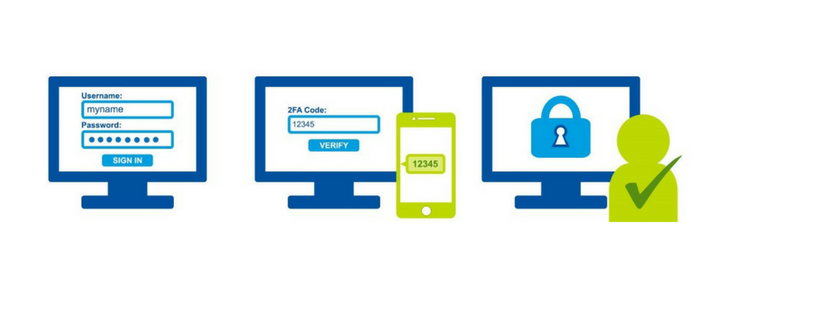
2FA stand for Two-Factor Authentication but can also be known as 2SA or Two-Step Authentication. 2FA is an extra layer of security that not only requires a password and username but also involves a ‘second step’ to confirm your identity. This second step requires you to use something that you have on hand, e.g. a phone or unique USB security key.
How does this work?
There are many different versions. Following are just three examples. You may be already using them without realising you are using 2FA.
1. Download an app specific to the organisation
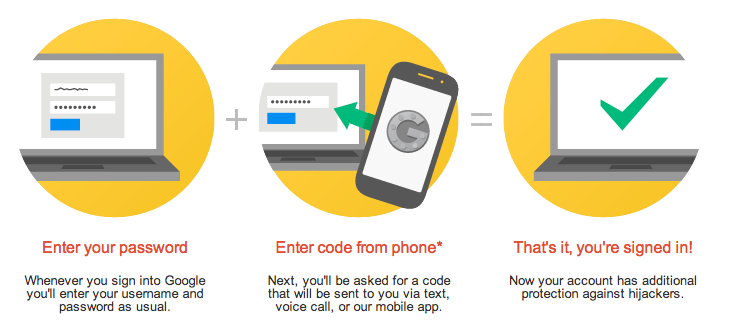
The organisation will have an app that you download to your smartphone or tablet. An example of companies that have this facility includes Google Authenticator, Microsoft Authenticator, or Xero ME. When you go to the organisations login page, you enter your username and password and then in the second layer of protection, a sequence of numbers will be sent that to your device which you key into the appropriate box.
Example from Google
2. In-built Authentication
You will often see this method when you log in to do online banking. Once you enter your username and password, another security screen will appear that will request you confirm that you wish to send a request for authorisation. A sequence of numbers will be sent to your device which you key into the appropriate box
3. Fingerprint Authentication
Similar to the other methods, you enter in your username and password and then using your smartphone, you scan your fingerprint as the second step verification.
What next?
Do a little research and see which organisation you use, have 2SF available and implement the function. Sit down and think about what you do online and you will see the value in implementing every available security method. It doesn’t matter which method you use; it is worth using 2FA for peace of mind.
The Money Edge | Bundaberg



.png)
.png)
.png)